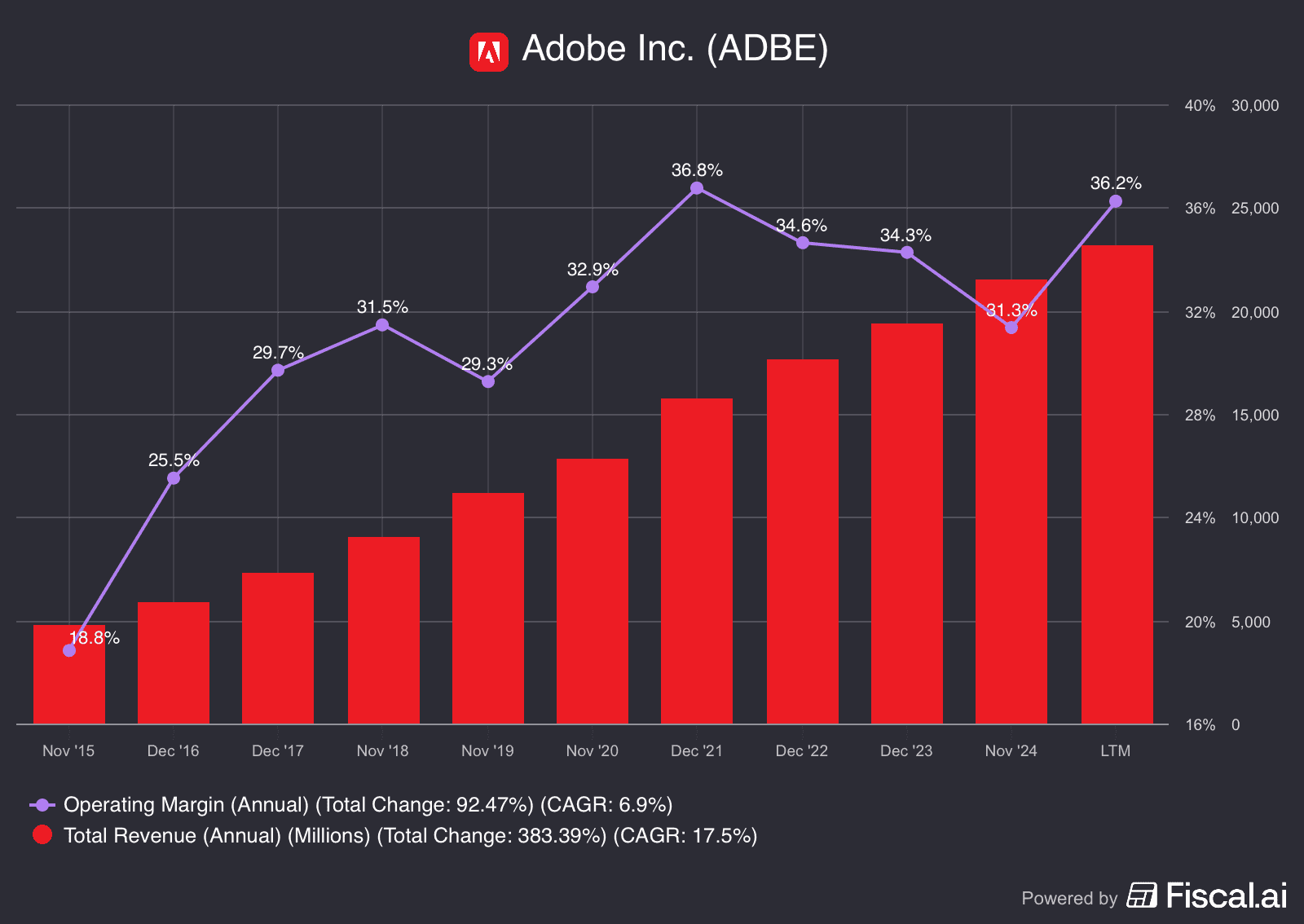
Most crypto traders have used permissionless blockchains like Bitcoin or Ethereum with out realizing there’s one other mannequin fully: permissioned blockchains. These personal networks run very otherwise, controlling who can be a part of, validate, and even see information. Understanding how each fashions work helps you choose a undertaking’s openness, safety, and development potential—a key ability for recognizing pink flags and making smarter funding selections.
The Significance of Understanding Blockchain Permission Fashions
Understanding the distinction between permissioned and permissionless blockchains will help you choose a undertaking’s credibility, transparency, and development potential. A community’s permission mannequin influences how open it’s to new individuals, how choices are made, and the way simply you possibly can entry or confirm data. Understanding these fundamentals enables you to spot dangers like centralization or low liquidity and determine whether or not a token or platform matches your funding technique. In brief, it’s a key a part of doing actual due diligence.
Learn extra: What Is Blockchain Know-how?
What Is a Permissioned Blockchain?
A permissioned blockchain is a non-public or semi-private community the place solely permitted individuals can be a part of, validate transactions, or view sure information. Entry is managed by a corporation or consortium, which units the principles for membership and governance. This setup is widespread in industries the place privateness, regulatory compliance, and management over information are important. For an investor, these blockchains typically energy enterprise options or tokenized property slightly than open, public cryptocurrencies.
Examples
Hyperledger Material: Utilized by corporations like IBM and Walmart for supply-chain monitoring.
R3 Corda: Designed for banks and monetary establishments to settle trades privately.
Quorum: A permissioned model of Ethereum initially developed by JPMorgan for enterprise use.
Benefits & Disadvantages
Permissioned blockchains supply a number of strengths. They will course of transactions sooner and at larger throughput as a result of they function with fewer nodes and lighter consensus mechanisms. Additionally they present stronger privateness controls, permitting solely permitted individuals to view or share delicate information. Verified identities make it simpler to adjust to rules, which is why these networks enchantment to banks and enormous firms.
On the similar time, permissioned blockchains have clear trade-offs. As a result of a single group or consortium units the principles, decentralization is diminished and governance may be much less clear. Exterior individuals have restricted visibility into exercise on the community, and the closed nature of those techniques typically means decrease liquidity or restricted entry to tokens for retail traders.
What Is a Permissionless Blockchain?
A permissionless blockchain is an open community the place anybody can be a part of, validate transactions, deploy sensible contracts, or just use the system with out prior approval. Principally, these are the blockchain networks everyone knows and love. These blockchains are decentralized by design and secured via financial incentives and cryptographic proofs slightly than belief in a government. For traders, they’re the spine of public cryptocurrencies, DeFi protocols, and Web3 apps.
Examples
Bitcoin: The unique public blockchain, used as a peer-to-peer digital foreign money.
Ethereum: The main sensible contract platform powering DeFi and NFTs.
Solana: A high-speed, low-fee blockchain for decentralized apps.
Avalanche: A community targeted on scalable, interoperable decentralized finance.
Benefits & Disadvantages
Permissionless blockchain networks give everybody equal entry, which fosters innovation and enormous consumer communities. They’re sometimes extra clear as a result of all transactions are public and verifiable. Decentralized governance additionally reduces reliance on a single authority, making networks more durable to censor or shut down.
Nevertheless, these strengths include trade-offs. World consensus mechanisms like proof-of-work or proof-of-stake can gradual transaction speeds and restrict scalability in comparison with personal techniques. Privateness is minimal by default, and regulatory compliance is more durable to implement as a result of individuals can stay pseudonymous.
Key Variations at a Look
Entry Management
Permissioned blockchains limit who can be a part of and validate transactions. Membership is granted solely after approval by the group or consortium working the community. This enables tight management over information and operations however limits participation and liquidity.
Permissionless blockchains are open to everybody. Anybody can obtain the software program, run a node, or work together with sensible contracts with out asking for approval. This openness helps bigger communities and extra innovation however may make networks more durable to control.
Keep Secure within the Crypto World
Learn to spot scams and shield your crypto with our free guidelines.

Identification
On permissioned blockchains, individuals are often recognized and verified, typically via KYC/AML checks. This creates a trusted surroundings the place transactions are tied to real-world identities, which is vital for banks and enterprises.
On permissionless blockchains, customers are both nameless or pseudonymous. Transactions are recognized by cryptographic addresses, not names. This protects privateness however can improve dangers reminiscent of fraud, scams, or regulatory uncertainty.
Governance
Permissioned blockchains use centralized or consortium-based governance. A small group of stakeholders units the principles, upgrades the community, and resolves disputes. This will make decision-making sooner however concentrates energy.
Permissionless blockchains depend on decentralized governance. Adjustments are proposed and adopted via group consensus, token-holder voting, or open-source improvement. This mannequin reduces single factors of failure however can decelerate upgrades and make coordination more durable.
Consensus Mechanism
Permissioned blockchains limit entry to a small, permitted set of validators, to allow them to use lighter consensus mechanisms reminiscent of Raft, PBFT, or IBFT. These are sooner and extra environment friendly as a result of they don’t must coordinate 1000’s of nameless nodes.
Permissionless networks depend on open participation, which requires extra sturdy, resource-intensive consensus strategies like proof-of-work (PoW) or proof-of-stake (PoS). These mechanisms safe the community without having belief in a central occasion however typically decelerate transaction finality.
Transparency
Personal blockchains (permissioned) restrict visibility. Solely licensed individuals can see transactions or delicate information, which fits companies that want confidentiality. Public audits are uncommon, and information sharing is selective.
In permissionless networks, the whole lot is clear by default. Transactions and sensible contracts are seen on public explorers, making it simpler for traders to confirm exercise and monitor funds. This openness builds belief however means there’s little privateness with out further layers.
Safety Mannequin
Permissioned blockchains depend on a trust-based safety mannequin. As a result of individuals are vetted, the principle threat is insider misbehavior slightly than large-scale assaults. Safety measures deal with entry management and compliance.
Permissionless networks use a trustless mannequin. Financial incentives and cryptographic proofs safe the system, making it proof against censorship or manipulation even when individuals don’t know one another. This method is stronger towards exterior assaults however can expose customers to scams or phishing as a result of identities are pseudonymous.
Scalability
In blockchain expertise, permissioned blockchains can scale extra simply as a result of they function with a restricted, permitted set of nodes. This smaller validator group lets the community deal with extra transactions per second and keep predictable efficiency.
Permissionless techniques must coordinate 1000’s of nodes unfold world wide. This decentralization strengthens safety however sometimes lowers throughput and makes scaling more durable with out extra layers or rollups.
Learn extra: Rollups in Crypto
Transaction Velocity
As a result of permissioned blockchains limit entry to trusted validators, they will verify transactions shortly. Fewer nodes and lighter consensus means sooner settlement instances, which is beneficial for enterprise or supply-chain functions.
In permissionless blockchains, anybody can take part. Whereas this openness is a key characteristic, it slows down transaction processing as a result of international consensus takes longer to attain. Excessive site visitors may result in congestion and better charges.
Privateness
Personal blockchains (permissioned) enable selective information sharing. Contributors can hold delicate data confidential whereas nonetheless benefiting from a shared ledger—a bonus for banks, healthcare, or regulated industries.
Permissionless blockchains are clear by default. All transactions are public, which helps with belief and auditability however affords little built-in privateness. Customers who want confidentiality should depend on privateness instruments, mixers, or specialised chains.
Immutability
In permissioned blockchains, immutability is configurable. As a result of a central administrator or consortium controls the ledger, they might reverse or amend information underneath particular circumstances (for instance, regulatory calls for or error correction). This flexibility advantages enterprises however reduces the “set in stone” high quality traders count on from public chains.
Permissionless blockchains, against this, supply sturdy immutability. As soon as a transaction is confirmed, it’s virtually unimaginable to change with out controlling many of the community. This permanence underpins belief in public cryptocurrencies.
Regulatory Compliance
Permissioned blockchains are simpler to align with regulation. Recognized identities and restricted entry enable KYC/AML procedures, auditing, and enforcement of knowledge privateness legal guidelines. This makes them enticing for monetary establishments and governments.
Permissionless blockchains are more durable to control. Nameless participation means compliance can’t be enforced straight, and regulators should deal with exchanges or service suppliers as a substitute of the core community. This freedom may be interesting to customers but in addition introduces authorized uncertainty.
Sensible Contract Management
In permissioned blockchains, sensible contracts are often deployed and ruled by community directors or the consortium. This ensures consistency and compliance however limits exterior innovation.
In permissionless blockchains, anybody can deploy sensible contracts with out approval. This openness fuels speedy development of DeFi and Web3 apps but in addition will increase the chance of unvetted or malicious code.
Examples
Permissioned blockchains: Hyperledger Material (provide chains), R3 Corda (banking), Quorum (enterprise Ethereum).
Permissionless blockchains: Bitcoin (digital cash), Ethereum (DeFi, NFTs), Solana (high-speed dApps), Avalanche (scalable DeFi).
Technical Structure Comparability
Now, let’s get just a little extra technical. Don’t click on off but—understanding how permissioned and permissionless blockchains truly run underneath the hood may be fairly vital even to common crypto traders, because it reveals the true limits, dangers, and alternatives of a undertaking. By taking a look at node setup, transaction validation, sensible contract management, and interoperability, you’ll see how a community’s structure can have an effect on pace, safety, decentralization, and in the end the worth of its tokens.
Node Operation and Onboarding
In a permissioned blockchain, node operators have to be permitted earlier than becoming a member of the community. They full id checks and obtain credentials or certificates that allow them run validator or observer nodes. This course of provides the community tight management over who maintains it, however limits openness and resilience.
In a permissionless blockchain, anybody can obtain the software program, sync the ledger, and turn into a full node or validator (in the event that they meet staking or {hardware} necessities). This open onboarding will increase decentralization and redundancy however could make coordination and governance extra complicated.
Transaction Validation and Finality
Permissioned networks use lighter consensus protocols reminiscent of Raft, PBFT, or IBFT. With fewer trusted validators, transactions verify shortly and attain deterministic finality in seconds.
Permissionless networks depend on resource-intensive consensus like proof-of-work or proof-of-stake. World participation slows block instances and affirmation, and finality is probabilistic or delayed till a number of blocks have handed. This design sacrifices pace for trustlessness and censorship resistance.
Sensible Contract Deployment and Management
In permissioned techniques, sensible contracts are deployed and managed by community directors or a governing consortium. Contracts might have pre-approval, code audits, or compliance checks earlier than activation. This offers consistency and regulatory alignment however limits exterior innovation.
On permissionless blockchains, any consumer can deploy a contract with out prior approval. This fuels speedy development of DeFi and Web3 apps but in addition permits unvetted or malicious code, inserting extra duty on customers and auditors.
Interoperability Issues
Permissioned blockchains typically use personal interfaces or customized requirements. Connecting them to different networks or public chains sometimes requires devoted gateways, APIs, or enterprise middleware. This will shield information however makes cross-chain communication slower and extra complicated.
Permissionless blockchains favor open requirements, public APIs, and broadly used token bridges. This openness eases interoperability with different public networks, but in addition introduces dangers reminiscent of bridge hacks or inconsistent safety throughout chains.
Use Circumstances
Listed here are some real-world examples of who’s constructing on every sort of blockchain and what they’re doing with it.
Permissioned Blockchains: Enterprise & Regulated Industries
IBM & Walmart (Hyperledger Material). Monitor meals merchandise throughout provide chains to enhance recall pace and transparency.
HSBC, ING, and different banks (R3 Corda). Settle interbank trades and handle syndicated loans privately.
JPMorgan (Quorum). Builds inside cost networks and tokenized asset platforms with regulatory oversight.
Healthcare consortia. Share affected person information securely amongst licensed suppliers whereas following privateness legal guidelines.
Permissionless Blockchains: Public Networks & Open Innovation
Bitcoin. Peer-to-peer digital foreign money with no central authority.
Ethereum. Platform for DeFi, NFTs, and decentralized apps.
Solana & Avalanche. Excessive-speed, low-fee environments for gaming, DeFi, and different Web3 apps.
Decentralized exchanges (Uniswap, SushiSwap). Run on permissionless chains to allow non-custodial buying and selling.
Can Permissioned and Permissionless Blockchains Co-Exist?
They already do. Many networks and corporations mix components of each fashions to stability openness with management:
IBM Meals Belief. Constructed on Hyperledger Material (permissioned) however anchors hash proofs of supply-chain information to a public blockchain for unbiased verification.
Vitality Internet Chain. Operates as a permissionless community for renewable-energy certificates however permits permissioned validator onboarding to fulfill regulatory requirements.
Central Financial institution Digital Currencies (CBDCs). Pilot initiatives such because the Financial institution of France’s digital euro or the Individuals’s Financial institution of China’s e-CNY typically run on permissioned infrastructures however use public or semi-public rails for interoperability with cost suppliers.
This hybrid method lets organizations hold delicate information personal, adjust to rules, and nonetheless profit from the safety, liquidity, and transparency of public blockchains. It additionally reveals that “permissioned” and “permissionless” aren’t mutually unique however slightly factors on a spectrum of design selections.
Permissioned vs. Permissionless Blockchains: Which One Is Higher?
Identical to with many different issues in life, there’s no single “finest” mannequin. What works relies on what a undertaking is attempting to attain. A community constructed for tightly managed workflows or delicate information will lean towards a permissioned design. That construction simplifies compliance, makes onboarding predictable, and lets directors implement privateness or regulatory guidelines from day one.
In contrast, a community that goals for open participation, broad token liquidity, or decentralized governance will profit from a permissionless method. This mannequin sacrifices some pace and management however creates transparency, resilience, and community-driven development.
Ultimate Phrases
Each permissionless blockchains and permissioned ones use the identical core expertise, however their entry, governance, and safety fashions produce very totally different trade-offs. Neither is universally “higher”. Studying extra about these techniques in addition to their benefits and downsides will help you higher perceive the crypto market as a complete, in addition to present some insights into institutional adoption of various blockchain sorts.
FAQ
What are the similarities between permissioned and permissionless blockchains?
Each use distributed ledger expertise to report transactions securely and depend on cryptography to keep up belief throughout a decentralized community of individuals.
Can a blockchain community be each permissioned and permissionless?
Sure, hybrid designs enable some options to be open like a permissionless blockchain whereas others are restricted underneath centralized governance or entry guidelines.
Which kind of blockchain is healthier for enterprise use?
Enterprises typically choose permissioned blockchains as a result of they provide managed participation, privateness, and compliance whereas nonetheless leveraging digital property and distributed ledgers.
Are permissionless blockchains much less safe than permissioned ones?
Not essentially. Permissionless blockchains acquire safety from broad decentralization, whereas permissioned networks depend on trusted validators and centralized governance for defense.
Is it potential emigrate from a permissioned blockchain to a permissionless one later?
Sure, but it surely’s complicated. Transferring to a permissionless blockchain entails reconfiguring consensus, id, and digital asset administration guidelines.
Which cash are utilizing permissioned/permissionless blockchains?
Most public digital property like Bitcoin and Ethereum run on permissionless blockchains, whereas personal tokens or consortium networks (e.g., Hyperledger-based initiatives) use permissioned blockchains.
How do I determine which blockchain mannequin is correct for my undertaking?
Consider your objectives, regulatory wants, and belief mannequin—permissionless blockchains go well with open, public techniques, whereas permissioned blockchains match managed environments with stronger centralized governance.
Disclaimer: Please be aware that the contents of this text will not be monetary or investing recommendation. The knowledge supplied on this article is the writer’s opinion solely and shouldn’t be thought-about as providing buying and selling or investing suggestions. We don’t make any warranties in regards to the completeness, reliability and accuracy of this data. The cryptocurrency market suffers from excessive volatility and occasional arbitrary actions. Any investor, dealer, or common crypto customers ought to analysis a number of viewpoints and be aware of all native rules earlier than committing to an funding.